Android optimizing apps are often deemed as smart, ambitious & high performing tools. Optimization tools are deployed on smart phones to improve device performance & eliminate storage issues. Hence, make the device more responsive & primed for any situation.
Reckoning the merits & popularity of android optimizing tools, manipulators pioneered a malware masquerading as a battery optimization tool to yank user’s chain.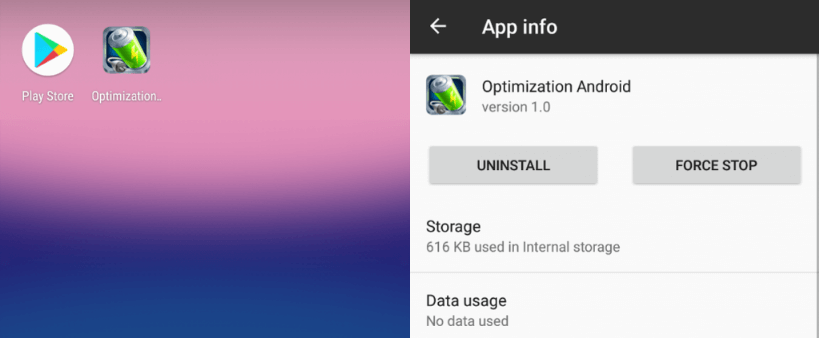
The nasty Trojan is distributed via third party app stores & not the official Google play Store. Users of official PayPal app act as a sitting duck for this gusty Trojan.
Threat Behavior of the Android Trojan
Once the rogue application is launched, it encounters you with an endless array of negatives. Its threat behavior can be categorized in two major parts.
Misuse of Android Accessibility Service to drain money from official PayPal App
During installation, the deceptive app requests access to Android’s accessibility permission to build a strong base. This request is presented to the user via Enable statistics service that appears unimpeachable.
If the user agrees to provide the app access to this utmost dangerous feature, it empowers the malevolent app to emulate taps & OS interactions.
The compromised device that has PayPal app installed lands in a pickle. The malware displays a notification alert prompting users to launch PayPal app. Once user logs in PayPal app, the Trojan abuses the Accessibility service to mimic screen taps to transfer money to attacker’s PayPal account.
The whole process takes around 5 seconds which leaves no feasible way for unsuspecting user to intervene. The process includes:
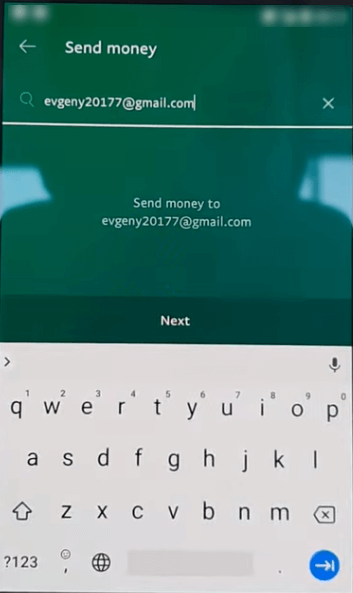
- Opening a new PayPal transfer
- Entering receiver’s PayPal account details,
- Entering the sum to be transferred
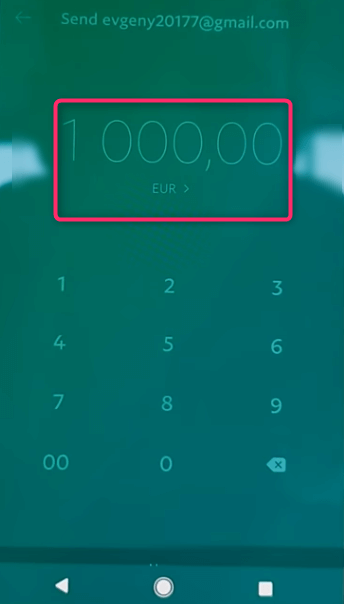
- Approving the transaction
The Trojan is coded such that the automated transaction takes place each time the user accesses their PayPal account.
Since the malicious script relies on users to log into the official payment app rather than stealing login credentials, those who have secured their PayPal app with two-factor authentication (2FA), are equally vulnerable as those not using 2FA.
Insufficient PayPal balance or no payment card connections to the account are the only two ways to fail the malign script.
Overlaying the screen of Legitimate apps with Phishing Screen
ESET security researcher Stefanko, who broke down this new Trojan’s features also reveled it’s other characteristic.
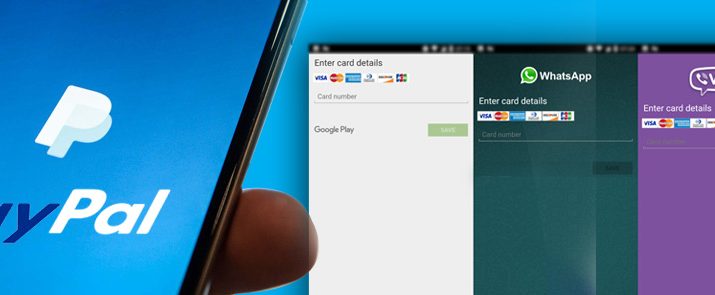
Besides the PayPal theft functionality, the malware is also scripted to leverage the popularity of some widely used legitimate app to overlay them with fishing screens to steal credit card details & login credentials.
The apps that are abused include:
- Viber
- Google Play
- Skype
- Gmail
Malicious overlay screens for Google Play, WhatsApp, Viber and Skype, request for credit card details. Pernicious overlay for Gmail seeks for Gmail credentials.
Other malefic overlay screens targeting few legitimate banking apps have also been detected. To prevent users from removing the overlay screen by pressing the back button or home buttons, the Trojan is cleverly scripted to display the phishing screen in lock foreground screen.
To get rid of the malicious overlay screen enter invalid data as wrong inputs make these screens disappear.
Other malevolent acts of this Android Malware
The malware is also capable of performing following menacing acts:
- Obtain Contact list
- Install app
- Run Installed app
- Make & forward calls
- Intercept text messages, delete SMS, and change the default SMS app.
- Start socket communication
Steps to avoid major harm by Android Malware
- Users are recommended to change passwords for banking apps, email account, social networking sites & PIN for cards at regular intervals of time.
- Report to the concerned authority for any unauthorized transactions.
- Users are advised to always read user reviews before installing any app. Positive reviews can be easily faked. Negative reviews are more likely to reveal the true nature of the app.
- Uninstall the suspicious apps ASAP using Android’s Safe Mode.
(130)